Apply machine learning techniques to detect malicious network traffic in cloud computing | Journal of Big Data | Full Text
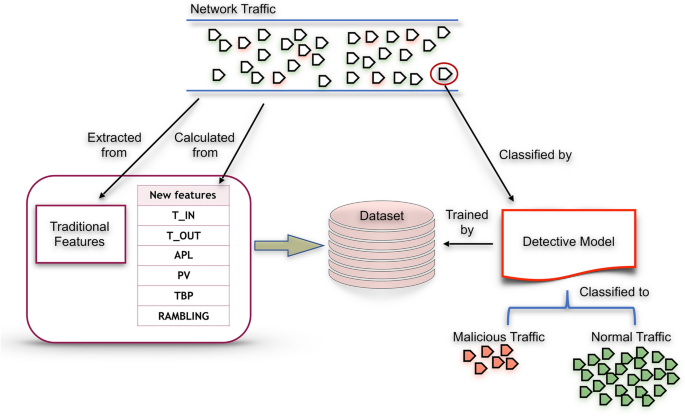
Apply machine learning techniques to detect malicious network traffic in cloud computing | Journal of Big Data | Full Text
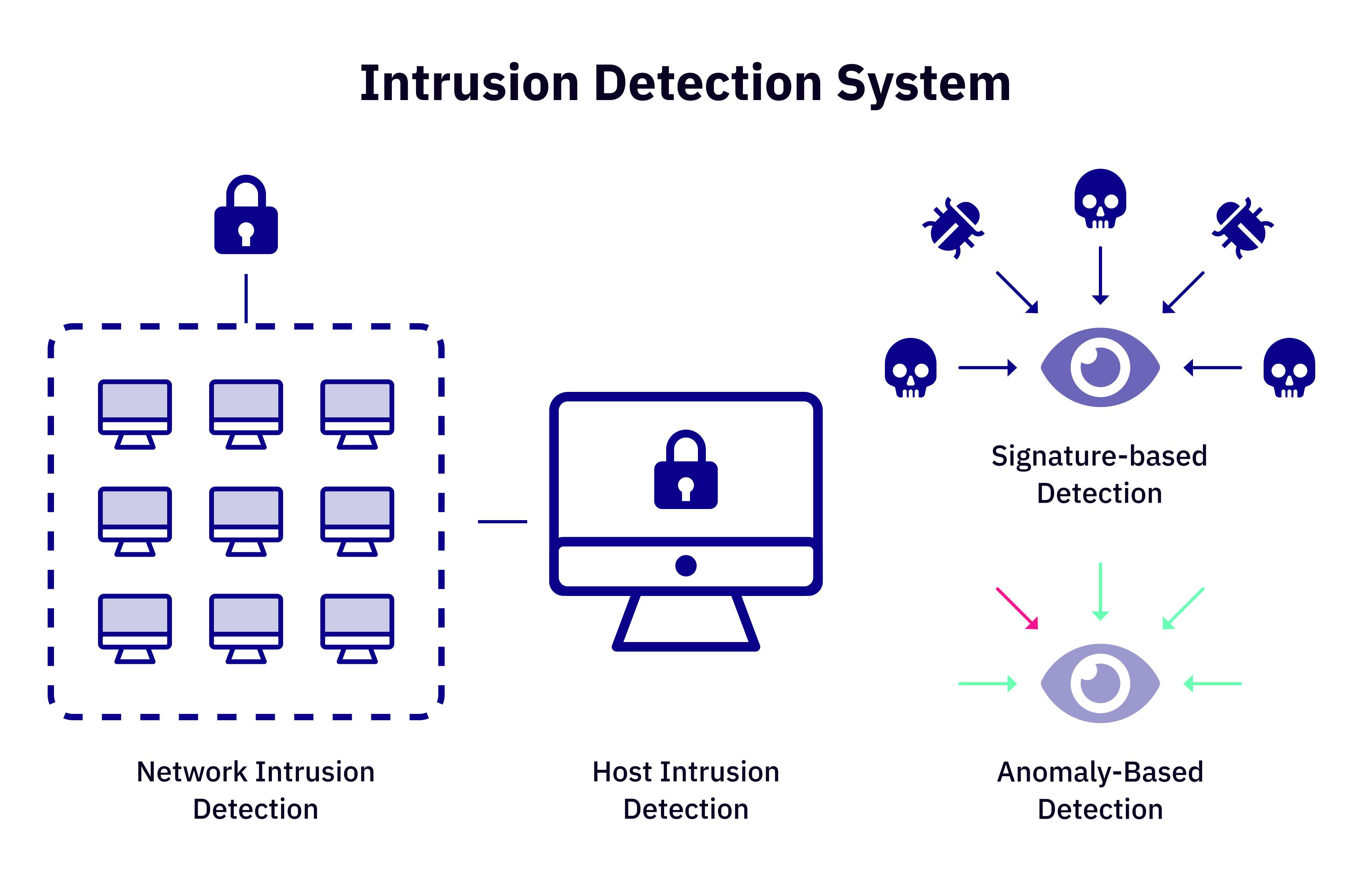
IDS and IPS for Kubernetes Intrusion Protection: Top 6 Solutions | IDS and IPS for Kubernetes Intrusion Protection: Top 6 Solutions

What Is Network Traffic Analysis? Definition, Importance, Implementation, and Best Practices - Spiceworks
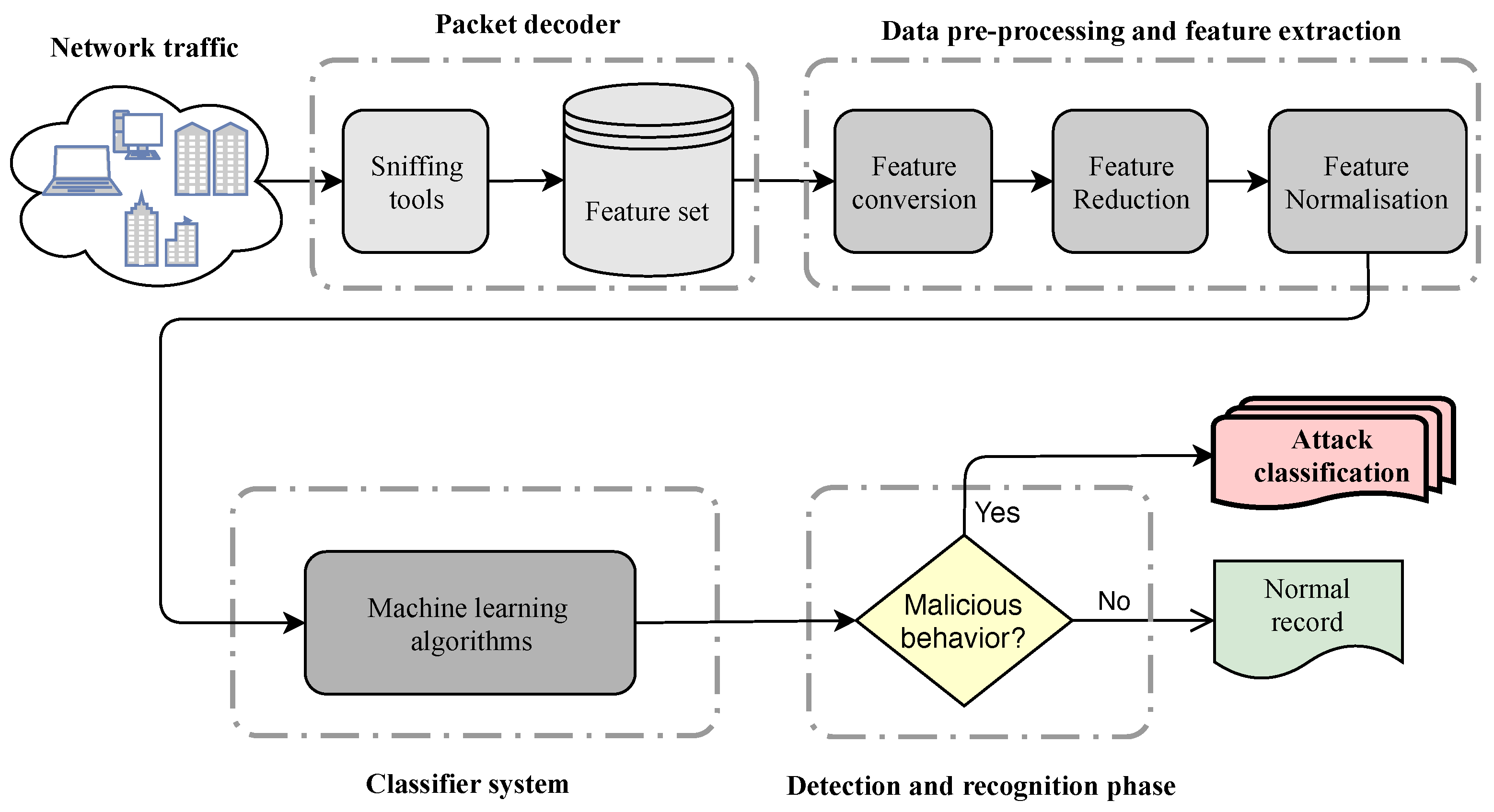
Entropy | Free Full-Text | A Review on Machine Learning Approaches for Network Malicious Behavior Detection in Emerging Technologies

Sensors | Free Full-Text | A Framework for Malicious Traffic Detection in IoT Healthcare Environment






![PDF] A Framework for Malicious Traffic Detection in IoT Healthcare Environment | Semantic Scholar PDF] A Framework for Malicious Traffic Detection in IoT Healthcare Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dffc01c21849a8f0634db790b0d2437464b03977/10-Table2-1.png)


![Maltrail Malicious Traffic Detection System - HackingPassion.com : root@HackingPassion.com-[~] Maltrail Malicious Traffic Detection System - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/maltrail-malicious-traffic-detection-system/featured-image.png)